Table of Contents
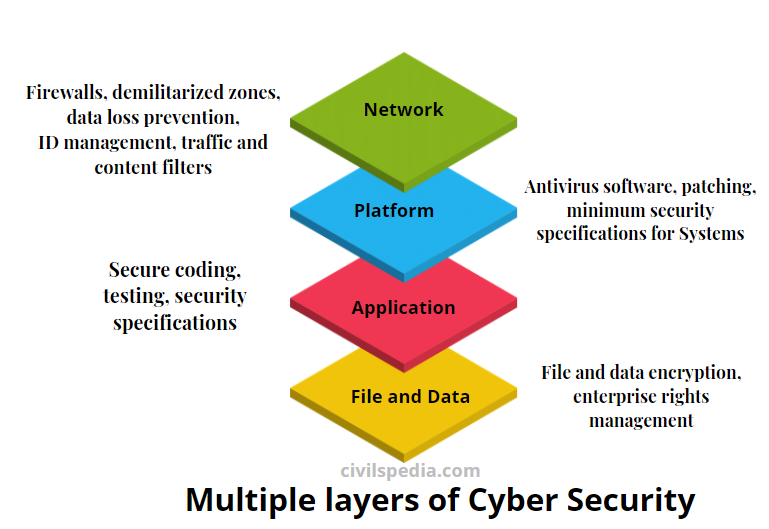
Basics of Cyber Security
This article deals with the ‘Basics of Cyber Security .’ This is part of our series on ‘Internal Security’, an important pillar of the GS-3 syllabus. For more articles, you can click here.
Introduction
- Information Technology Act of 2000 defines Cyber Security as “protecting information, equipment, devices, computer resource, communication device and information stored therein from unauthorized access, use, disclosure, disruption, modification or destruction.”
- The internet is prone to attacks as its architecture was designed to promote connectivity and not security.
- With the growing importance of the internet, cyberspace has been recognized as 5th dimension of warfare (after land, sea, air and space)
- The importance of the internet in India can be gauged from the following data.

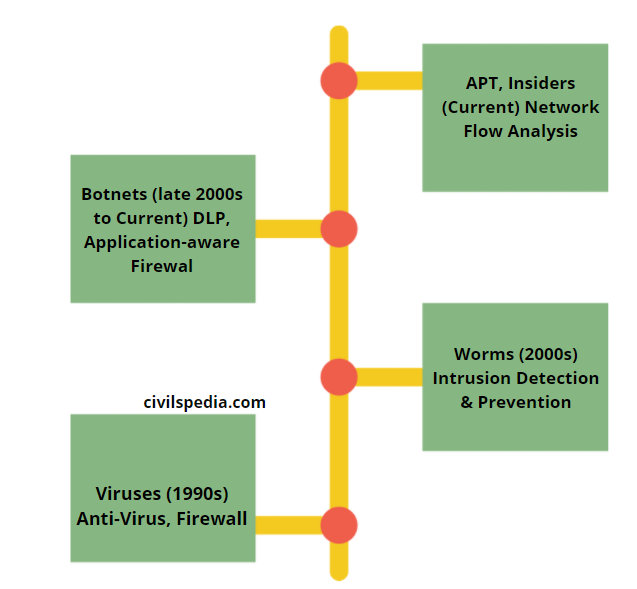
Evolution of Cyber Security
Cyber Security Threats

1. Cyber Crime
- There is no fixed definition of cybercrime. It refers to all the criminal activities done using the computer, the internet and cyberspace. Even the Indian IT Act doesn’t define cybercrime.
- Cybercrime is an intellectual and white-collar crime.
- Generally speaking, it can be divided into two categories i.e.
- Crimes that target computers and devices directly. E.g., Hacking, computer viruses, data theft, Denial of Service (DoS) attacks etc.
- Crimes facilitated by computer networks. E.g., Phishing, Spam, Offensive Content, Cyber Stalking etc.
- The most prominent form of cybercrime is identity theft, in which criminals use the internet to steal personal information from other users. Two of the most common ways this is done are phishing and pharming.
- Cyber Crime is a broader term which includes Cyber Attacks, Cyber Terrorism and Cyber Warfare.
2. Cyber Attack
- Cyber-attack is “any type of offensive manoeuvre employed by individuals or organizations targeting computer information systems, infrastructures, and computer networks with a goal to alter, disrupt, deny, degrade, or destroy the data held on the targeted system or network.”
- It is mostly done using malicious code.
- International examples of Cyber Attacks include
- SolarWinds cyberattack (2020) in which hackers exploited the loophole in SolarWinds Orion software, which is used by thousands of companies, including several US government agencies.
- Ransomware attack on ‘Colonial Pipeline Company’ for which it paid millions of dollars in Bitcoins
- In 2012, Saudi oil major Aramco was hit by the ‘Shamoon virus‘, which wiped the memory of 30,000 computers. The attack was likely carried out by Iranians.
- Some notable examples of cyber attacks on India include
- Pakistani Hackers, “Pakistani Cheetahs“, frequently try to hack the government of India websites.
- In 2020, the Chinese hacker group Stone Panda attacked the Serum Institute of India (SII) and Bharat Biotech’s IT systems to access data related to the Covid-19 vaccine developed by these companies.
- 32 lakh debit cards of the consumers of Indian banks were compromised in 2016.
3. Cyber Terrorism
- The acts of terrorism related to cyberspace or executed using cyber technologies are popularly known as ‘cyber terrorism’. It is the convergence of terrorism and cyberspace.
- The basic qualifier to be recognized as cyber terrorism is that attack should result in violence or generate fear.
- In 1998, Sri Lankan embassies were swamped with e-mail bombs by ethnic Tamil militants. It is believed to be the first cyber terror attack in the world.
4. Cyber Warfare
- Cyberwarfare is the use of computer technology in politically motivated attacks against a state or organization. It includes targeted attacks on information systems for tactical or strategic reasons.
- Cyber warfare attacks can disable official websites and networks, disrupt or disable essential services, steal or alter classified data, and cripple financial systems among many other possibilities.
- Any country can wage Cyberwar on any other country, irrespective of resources, because most military forces are network-centric and connected to the internet, which is not secure. For the same reason, Non-Governmental Groups and individuals could launch cyber warfare attacks.
International Examples
- Stuxnet attack in 2010 in which Israel attacked Iranian Nuclear Plants.
- In 1998, the United States hacked into Serbia’s Air Defence System to compromise air traffic control and facilitate the bombing of Serbian targets.
- In 2012, large-scale cyber attacks targeted at the Iranian government were uncovered. In return, Iran is believed to have launched massive attacks aimed at US banks and Saudi oil companies.
Indian Examples
- 2020: During the Galwan Valley incident with China, the Chinese hacker group Red Echo conducted a “ShadowPad” malware attack against India, resulting in a massive power outage in Mumbai.
- When violence broke out in 2012 between residents of Assam and Bangladeshi migrants, nationwide hate messages were spread by Pakistan.
5. Cyber Espionage
- Cyber Espionage is the act or practice of obtaining secrets without the permission of the holder of the information, from individuals, competitors, rivals, groups, governments and enemies for personal, economic, political or military advantage using methods on the internet, networks or individual computers through malicious software including Trojan Horses and Spywares.
- These acts are between state nations, but they may include non-state actors too.
- Examples include
- In 2020, Indian Express Investigation found that Zhenhua Data Information Technology Co. was monitoring over 10,000 Indian individuals and organizations, including bureaucrats in key positions, judges, scientists and academicians, journalists, actors, sportspersons, religious figures and activists.
- NSA Surveillance Program as revealed by Edward Snowden in the USA.
- Cyber-espionage group called Danti penetrated Indian government systems.
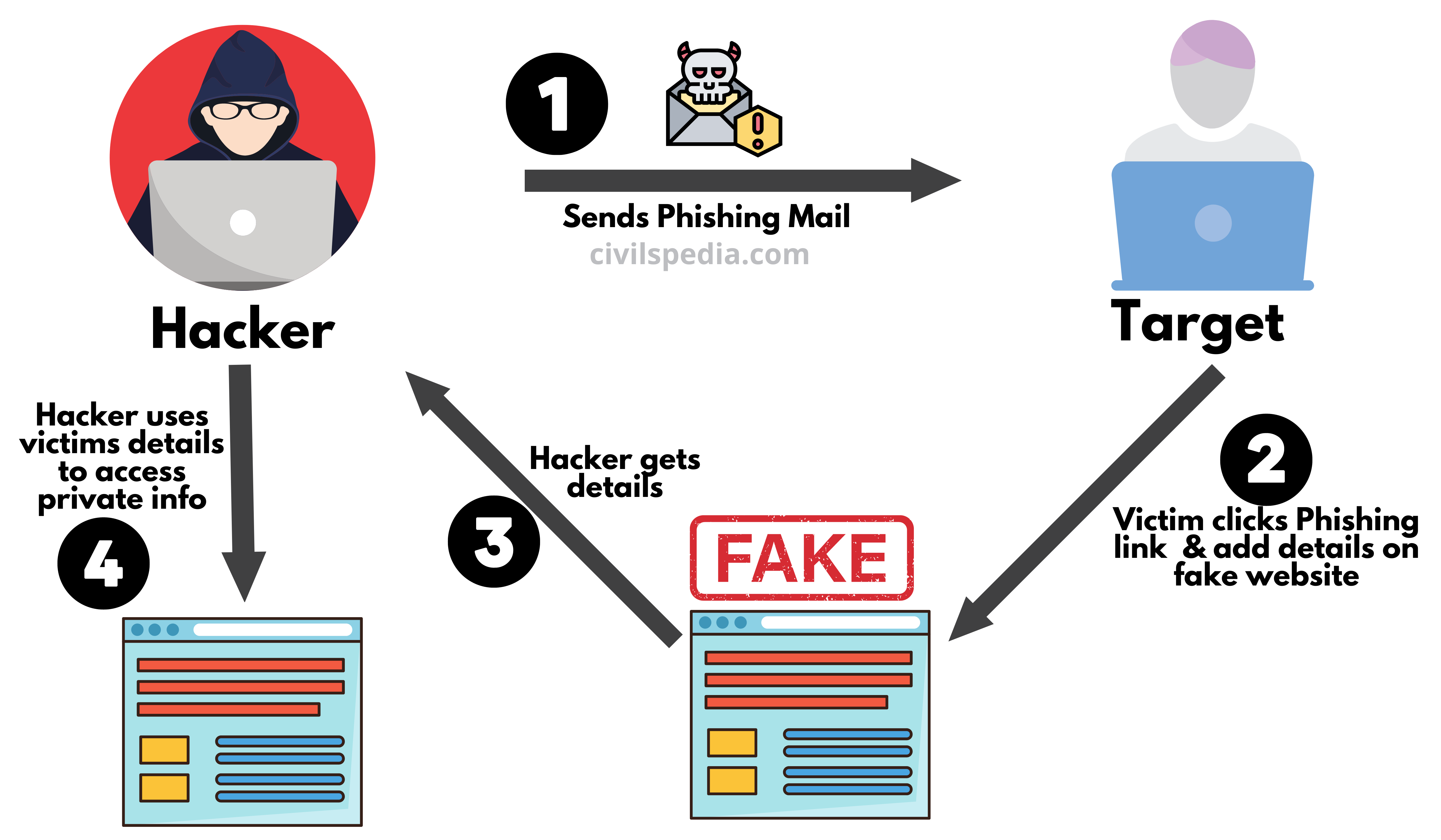
6. Phishing
- Phishing websites or web pages are created by fraudsters, which leads you to believe you are entering your personal details on a secure website, but the details go directly to the fraudster.
- Using these details, the fraudsters can log in from your account and change the password, locking you out of your own account or using the credit or debit card details and password to withdraw money.
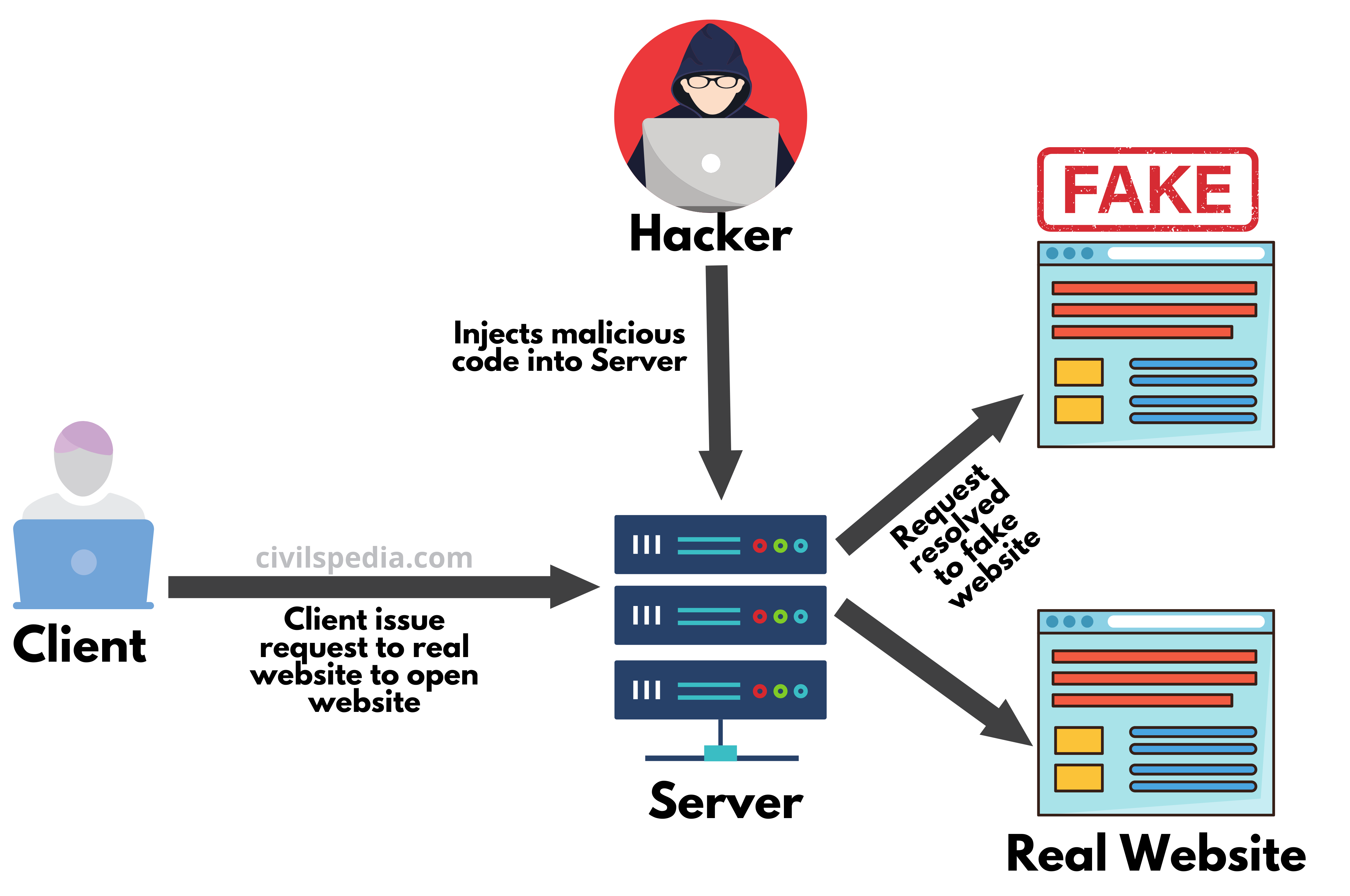
7. Pharming
- Pharming is a type of scam wherein malicious malware is loaded on a server to trick people into visiting fraudulent websites without their knowledge or consent.
8. Crypto Jacking
- Crypto-Jacking is a process in which unauthorized crypto-coin miners siphon the resources of personal computers to mine cryptocurrencies like Bitcoin without the owner’s knowledge.
- According to the latest Symantec Report, this is the latest major threat in cyber security.

9. Cognitive Hacking
- Cognitive Hacking involves exploiting psychological vulnerabilities, perpetuating biases, and compromising logical and critical thinking to change the target audience’s thoughts and actions, galvanize societies and disrupt harmony using disinformation.
- Cognitive Hacking tries to manipulate the way people perceive reality.
- Examples
- A group named QAnon spread false information arguing that the US 2020 presidential election was fraudulent.
- Conspiracy theorists in countries like UK and Netherlands burnt down 5G towers believing that it caused the novel coronavirus pandemic.
Malware
Malware is a term used to describe harmful software that is capable of monitoring users’ online activity without their consent.
1. Computer Virus
- A computer virus is a computer program developed by a programmer to infect other programs.
- It affects the computer system in the following ways
- Destructs file allocation table (FAT)
- Erases specific programs and data on discs
- Alters content of files
- Suppresses execution of RAM
- Destroys part of data held on disc via the creation of bad sectors
- Formats discs or tracks on discs in a different way.
2. Trojan Horses
- A Trojan horse is a malware program, which seems to be doing one thing, but in reality, it does another thing and is used to set up a rear door into the system, thereby enabling the intruder to access the user’s personal information.
3. Spyware
- It is a computer program that gathers personal information secretly and sends it via the internet from the computer without the user’s knowledge.
- E.g., Spyware called Pegasus (made by an Israeli firm, NSO) is used by various government agencies to compromise the phones of multiple activists, journalists and lawyers.
4. Ransomware
- Ransomware, as the name suggests, locks computers, encrypts the data on them and prevents users from accessing their devices and data until a certain ransom is paid to its creator.

Examples
1 . WannaCry (2017)
- WannaCry ransomware attack infected more than 1 lakh companies and services, including the National Health Services (NHS) of Britain, where doctors were blocked from patient files. Hackers demanded $300 in Bitcoins to decrypt files.
2. Petya (2017)
- Petya was even more advanced ransomware than WannaCry. Its chief targets were Ukraine and Russia.
3. Colonial Pipeline Company Attack (2021)
- Ransomware attack on ‘Colonial Pipeline Company’ for which it paid millions of dollars in Bitcoins
5. Spam
- Spam in the security context is primarily used to describe e-mail spam—unwanted messages in your e-mail inbox. Spam, or electronic junk mail, is a nuisance as it can clutter your mailbox and potentially take up space on your mail server.
Associated Terms
1. Hacker
A “clever programmer” or “someone who tries to break into computer systems to steal personal data without the owner’s permission or knowledge” is known as a Hacker.
2. Firewalls
- A device that guards the entrance to a private network and keeps out unauthorized or unwanted traffic is termed as Firewall.
- Firewalls distinguish “good” traffic from “bad” traffic.
3. Encryption and Decryption
- Encryption is the process of translating the plain text into random and mangled data (called cipher-text).
- Decryption is the reverse process of converting the cipher-text back to plain text.
- Encryption and decryption are done by cryptography.
- Encryption is used to protect data in a communication system, for example, data being transferred via networks (e.g. the internet, e-commerce etc.), mobile telephones, wireless microphones, wireless intercom systems, bluetooth devices and bank automatic teller machines.
- WhatsApp uses end-to-end encryption that ensures only you and the person or group you are communicating with can read and see what is sent, and nobody in between — not even WhatsApp have access to messages. Investigators argue they’re creating warrant-proof spaces for criminals. When no such absolute privacy exists in the physical world, how can such exist in the virtual world?
- Strong encryption protocols increase consumer confidence in the digital economy, but the Indian government fears a scenario where criminals or terrorists can easily “go dark” behind secure channels.
Benefits of Cyber Attack over Conventional Attack
- Cheaper to execute.
- Less risky as no physical harm can be done to the attacker.
- Anonymity, as technology, permits the attacker to conceal its origin, making it more lucrative for the state and non-state actors.
- These attacks are unconstrained by distance.
- Several people can use the same program.
- Traditional security concepts like deterrence and retaliation are challenging to apply.
- Difficult to locate the attacker, who can even mislead the target into believing that the attack has come from somewhere else.
India’s vulnerability in Cyber Space
India remains vulnerable to digital intrusions such as cyber-espionage, cybercrime, digital disruption and Distributed Denial of Service. India is the 3rd most vulnerable country in the world in terms of cybersecurity breaches, followed by US & China (according to a 2018 Report by Symantec).
- Indian IT Act of 2000 is weak with the presence of large lacunae (explained below).
- Cyber Security audits do not occur periodically, nor do corporations adhere to international standards.
- There is a lack of best practices and statutory backing for the same in India. E.g., norms for disclosure of cyber attacks were only put in place in 2019.
- There is no data protection law in India.
- Data Colonization of Indian data is happening at a great pace as Indian data is exported abroad and stored outside in the absence of data localization law.
- The multiplicity of agencies (more than a dozen), including MHA, CERT-IN, NCIIPC, State police etc., deal with cybercrime. The lack of coordination hinders smooth functioning.
- Computer Emergency Response Team (CERT-In) is woefully understaffed.
- Chinese are increasing their military capacity for the cyber attack, which is a cause of concern for India.
- Most mobile devices are made in China, which heightens the risk of Cyber Espionage.
- At the individual level, there is attitudinal apathy of users towards issues of cybersecurity. Indians don’t use paid original versions of operating systems and software. As a result, they don’t get frequent updates from the system, making them vulnerable to cyber-attacks.
Why does India need Cyber Security?
- India is betting big on the digital sector. Cyberspace has become a key component in the formulation and execution of public policies such as Digital India & Smart Cities. Hence, an ultra-secure cyber network is required in India.
- The number of internet users in India is increasing at an unprecedented pace. In 2020, India had nearly 730 million Internet users, which will grow to over 974 million users by 2025.
- The government’s digital push, especially promoting programs such as Aadhar, Digilocker, e-Market etc., makes cyber security very important. In these schemes, the government is processing and storing sensitive data, which, if compromised, can have a devastating impact.
- The number of cyber crimes is also rising at a fast pace, as corroborated by the fact that National Crime Records Bureau (NCRB) in 2019 registered a 63.5% jump in cybercrime cases over 2018. Additionally, the frequency of highly sophisticated cyber attacks like Wannacry and Petya is rising.
- To protect our Critical Infrastructure.
- To protect the private sector, especially the IT sector, which is an important job creator and source of foreign exchange.
- To protect the citizens of the nation from hacking & fraud attacks.
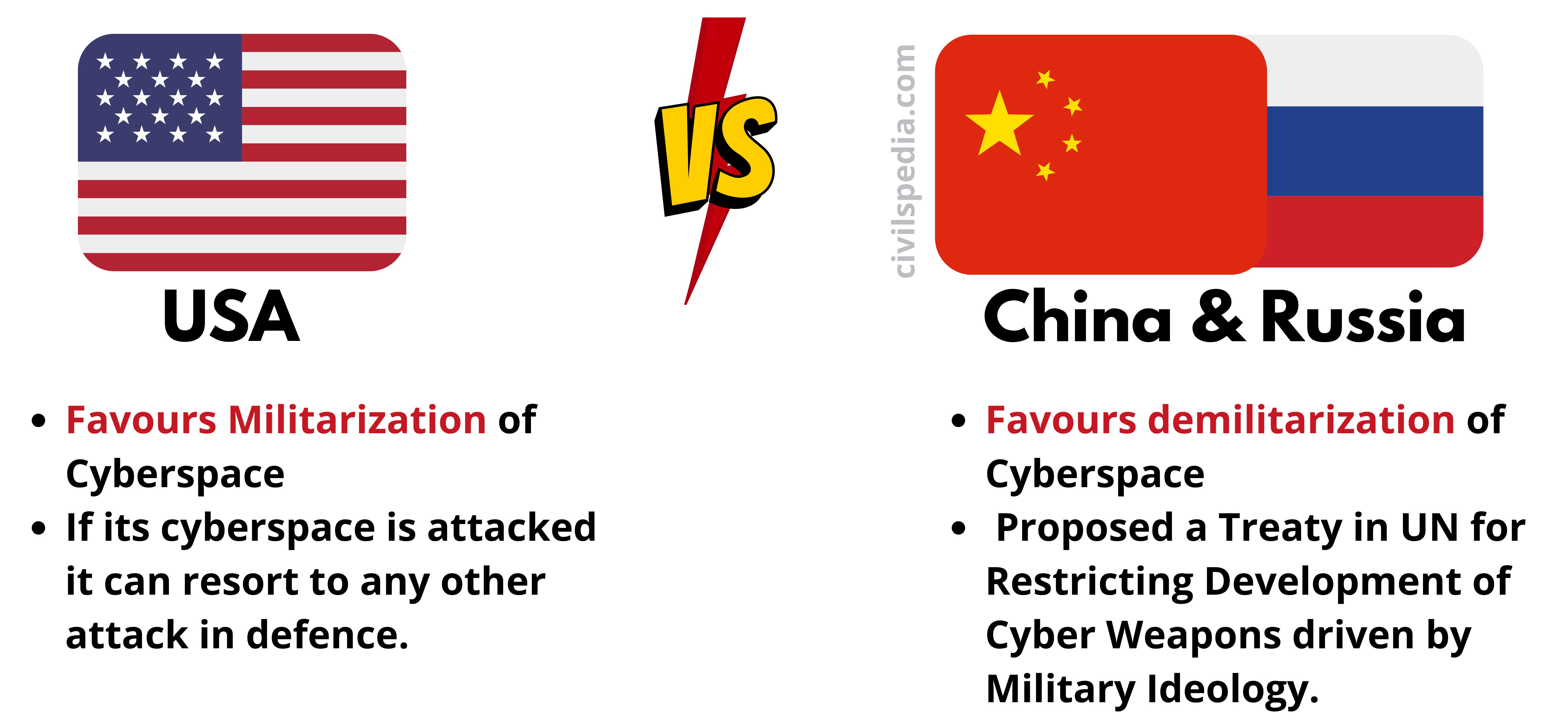
- Most countries are going for the militarization of cyber space, which can alter the outcomes of the battle.
Side Topic: Stand of various nations on the militarization of cyberspace
India’s Cyber Security Architecture
1. IT Act,2000
Information Technology Act of 2000 regulates the use of computer systems and computer networks and their data. The act gives statutory recognition to electronic contracts and deals with electronic authentication, digital signatures, cybercrimes, the liability of network service providers etc.
Act declares the following things as cyber crimes
| Section 66A | Sending offensive messages through a communications provider, including attachments. |
| Section 66B | Dishonestly receiving stolen communication devices or computer resources. |
| Section 66C | Identity theft |
| Section 66D | Cheating by personating |
| Section 66E | Violation of privacy |
| Section 66F | Defines Cyber Terrorism: As the act of causing a denial of service, gaining unauthorized access, or introducing a virus in any critical information infrastructure of the nation as defined by Section 70 with the purpose of endangering India’s unity, integrity, security, or sovereignty, terrorizing the general public, or gaining unauthorized access to data or databases that are restricted for the sake of the state’s security or friendly relations with foreign states. |
| Section 67A | The electronic publication or transmission of material having explicit sexual content. |
| Section 67B | Publishing or distributing content that shows children in sexually explicit acts. |
Along with that, the IT Act of 2000 has provisions for the creation of NCIIPC and CERT-In.
- Section 70A: Creates NCIIPC (National Critical Information Infrastructure Protection Centre) to protect Critical Information Infrastructure (CII) (12 sectors like banking, defence, aviation etc.)
- Section 70B: Creates ‘Computer Emergency Response Team India’ (CERT-IN) modelled on a similar force in the USA to deal with cyber security threats like Hacking and phishing and strengthen defence.
However, the act is weak in the following issues.
- The maximum damage, by way of compensation, stipulated by the cyber law amendments is Rs.5 crores. It is a small amount to act as a deterrent for corporates.
- The issue of spam has not been dealt with comprehensively. The word ‘spam’ is not even mentioned anywhere in the IT Act. It is pertinent to note that countries like the USA, Australia and New Zealand have demonstrated their intentions to fight against spam by making laws specifically dealing with spam.
- Indian information technology (IT) laws are not stringent enough to deal with hacking instances. In case someone gets hacked by any university or institute network, the maximum punishment is three years and Rs. 5 lakhs under Section 66.
- Hacking is a bailable offence in India, unlike the US.
- In the US, when the Sony PlayStation network was hacked, users filed lawsuits against the company. In India, users who lost their data could do nothing against the company. A low-level police inspector investigates cyber crimes like data hacking in India. The efficacy of such an approach is hardly likely to withstand the test of time, given the current non-exposure and lack of training of Inspector level police officers to cyber crimes.
- The act does not protect privacy. Hence, it does not prevent companies from selling or sharing consumer data.
- The bill also does not comprehensively define cyberterrorism.
The government has tried to update the bill to deal with the challenges of cyberspace. The dynamic nature of the sector means that the government is always playing catch up.
2. National Cyber Security Policy, 2013
It was brought against the backdrop of revelations by Edward Snowden of the massive NSA surveillance program.
Salient features of Policy
- Set up a 24×7 NCIIPC to protect the critical infrastructure of the country.
- Create a taskforce of 5 lakh cyber security professionals in 5 years.
- Provide fiscal advantages to businesses for the adoption of standard cyber security practices.
- Designate CERT-In as in charge of cybersecurity-related matters and have the local (state) CERT bodies coordinate at the respective levels.
- Develop a dynamic legal framework to deal with Cyber Security.
- Set up testing labs to regularly check the safety of equipment
It has to be noticed that National Cyber Security Policy 2013 mainly covers defensive and response measures and makes no mention of the need to develop offensive capacity.
3. CERT-In
- CERT-In (Cyber Emergency Response Team – India) was constituted under IT Amendment Act, 2008.
- It works under the aegis of the Ministry of Electronics and Information Technology (MEITY).
- Its main functions include
- Act as the national agency in charge of cyber security.
- Identify cyber threats and issue warnings.
- Respond to cyber security incidents as and when they occur.
- Coordination of cybersecurity threat response.
- Issuance of guidelines, advisories, vulnerability notes and white papers relating to Cyber Security.
It has to be noted that CERT-Fin has also been established to tackle threats related to the financial sector.
4. NCIIPC
- National Critical Information Infrastructure Protection Centre (NCIIPC)is the nodal agency to protect the country’s critical infrastructure like banking, defence etc.
5. I-4C
- It works under the Ministry of Home Affairs.
- It helps to tackle internet crimes such as cyber threats, child pornography and online stalking.
6. CyCord Centre
- It was formed in 2018.
- It is a platform for Law Enforcement Agencies to collaborate and coordinate their efforts to resolve cyber crimes.
7. Cyber Swachhchta Kendra (CSK)
- It is a part of the Digital India Initiative.
- At CSK, computer systems are scanned by CERT-In for free.
- It also enhances the awareness among citizens regarding botnet and malware infection.
- CSK provides various tools to prevent cyberattacks, like-
- M-Kavach: Antivirus for smartphones.
- USB Pratirodh: USB protector
- Browser JSGuard: Block malicious JavaScript and HTML files.
- Free Bot Removal Tool (made in collaboration with QuickHeal).
- AppSamvid: Whitelisting tool for the desktop.
8. State Specific Steps
Various states are also taking steps wrt Cyber Security
| Telangana | – Telangana is the first state to come up with a policy on cybersecurity. – It has also established a Cybersecurity Center of Excellence (CCoE). |
| Kerala | Cyberdome is a Center of Excellence for Kerala Police to bridge the gap between the latest changes and innovations in cyberspace and the skill set development of Kerala Police. |
| Maharashtra | Maharashtra has become the first state in the country to have a cyber-police station in each district |
9. Other Steps
- I4C has launched Cyber Crime Volunteer Program to allow citizens to register themselves as ‘unlawful content flaggers’ to report online content for removal and help law enforcement agencies.
- India is working with the UK, USA, China, Malaysia, Singapore, Japan and many other countries on diverse issues such as joint training of cybersecurity professionals, information exchange, law enforcement and technical capacity building to combat cybercriminal activities jointly.
- 52 countries (including India) and international bodies have signed the Christchurch Call to Action to eliminate terrorist and violent extremist content online.
Budapest Convention
| Came into force | 1 July 2004 |
| Against | 1. Crimes committed via the Internet 2. Infringement of copyrights 3. Computer-related fraud 4. Child pornography 5. Violation of network security |
| Objective | – Pursue common criminal policy aimed at the protection of society against cybercrime by adopting legislation – Declare any publication of racist or xenophobic propaganda via computer network an offence |
Developing countries, including India, have not signed it, stating that the developed countries led by the US-drafted it without consulting them.
Steps India should take
- Individual Level: Individuals should be educated to create backups & also understand the need for them. They must be educated not to reveal their sensitive personal information indiscreetly.
- Amendment of IT Act 2008, which should include provisions like
- Data Localisation
- Security certification’ for important network equipment and software companies.
- Using Cloud Computing: Since small firms, startups and government departments can’t buy expensive firewall systems individually, the government can go for Cloud Computing (IaaS) Mechanism to provide high-end and secure firewalls. It will reduce the price and increase affordability.
- Cyber Offensive Policy: India should have its own Cyber Offensive policy to give a clear idea to the world of how India would respond if any nation-sponsored Cyber Attack hits it.
- India can raise a cyber command of the Indian Military to combat cyber warfare.
- Sign Budapest Convention – Budapest Convention is the first & only international treaty that addresses Internet and computer crime.
- Air gapping: Air gapping isolates a computer or network and prevents it from establishing an external connection.
- Using Quantum Cryptography: Cryptography is the process of encoding and decoding information so that it is sent securely over the communication network. Present Systems of Cryptography use Mathematical Algorithms which can be cracked. Quantum cryptography uses the spin of photons as the key. Hence, there is little chance it can be cracked.