Linkages of Organized Crime with Terrorism
This article deals with ‘Linkages of Organized Crime with Terrorism.’ This is part of our series on ‘Internal Security’, an important pillar of the GS-3 syllabus. For more articles, you can click here.
Introduction
Like terrorism, there is no single uniformly accepted definition of organized crime. Even UN Convention against Transnational Organized Crime does not define organized crime.
According to Interpol, an Organized Crime Group can be defined as ‘any group having a corporate structure & whose primary objective is to obtain money through illegal activities, often surviving on fear and corruption.’
Characteristics of Organized Crime Groups
1. Continuity
- These groups are structured to survive leadership changes. Due to their structured nature, they operate beyond an individual’s lifetime.
2. Structure
- These groups are highly structured with a properly defined hierarchy. The ranks are based on power and authority.
3. Membership
- Their membership is restricted and based on common traits like ethnicity, background, common interest or proximity with the leader. Scrutiny and probation are crucial parts of member recruitment.
4. Criminality
- Such groups rely on criminal activities to generate income. Therefore, these groups are engaged in criminal activities like smuggling, murder, intimidation, drug trafficking, human trafficking etc.
5. Violence
- These groups use violence against opposition groups to protect their commercial interests.
6. Intimidation
- To get their job done, criminal gangs indulge in intimidation against people or public officials.
7. Corruption
- Crime thrives in a corrupt atmosphere. Organized Crime Groups buy off law enforcement officers to carry out their illegal activities without resistance.
8. Power & Profit Motives
- All the actions of the Organized Crime Group aim to maximize the group’s power and profits. For this, the group bribes the officials and leaders and even indulge in intimidation and violence.
9. Protectors
- These groups have protectors in the form of public officials, attorneys and businessmen who collectively protect the criminal group.
10. Specialist support
- These groups are assisted by specialists on an ad-hoc basis, including chemists (in the drug business), shooters (for murder), pilots (in smuggling) etc., who are nonetheless considered part of the group.
The degree of these characteristics may vary from group to group. However, the quintessential element of organized crime is continuing illegal activities to generate illegal proceeds.
Famous Organized Crime Groups of the World
| Country | Organized Group | Important Points |
| Japan | Yakuza | – Transnational Crime Syndicate with more than 28,000 members and a turnover of around $50 billion. It further has three more clans, i.e. Yamaguchi Gumi, Sumiyoshi-kai and Inagawa-kai. |
| Italy | Ndrangheta group | – It has an annual turnover of €53 billion. – It is engaged in wide-ranging activities like murder, extortion, drug trafficking and money laundering. They control the supply of cocaine in the whole of Europe. – Membership relies on blood ties in the Calabria region of South Italy. |
| USA | CRIPS | African-American Organized Criminal Group in USA with a turnover of $8 billion |
| India | D Company | – D Company is named after its leader Dawood Ibrahim. – It is the most powerful gang in Mumbai with abroad networks. – It is involved in extortion, narcotics, drugs, smuggling and contract killing. |
| Russian | Mafia | |
| Hong Kong | Triads |
Main activities carried by Organized Crime
1. Drug Trade
- It is the biggest revenue source for most organized crime groups.
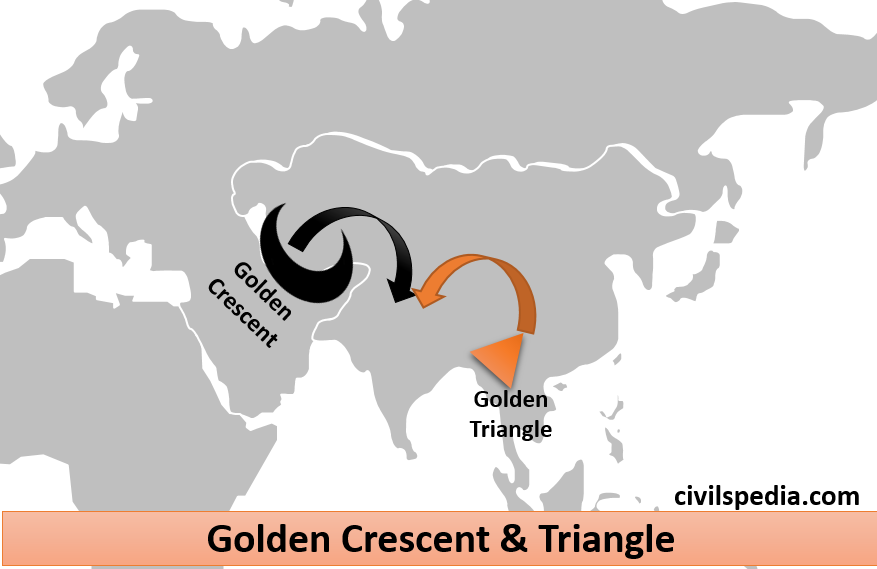
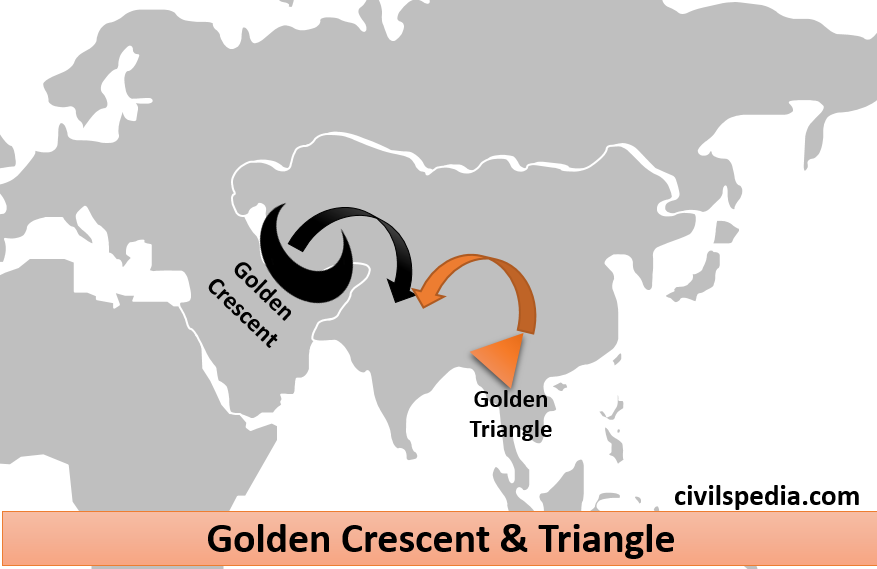
- It is quite widespread in India due to India’s geographical location between the golden triangle and golden crescent, the world’s leading producers of narcotics.
- Apart from that, opium is legally cultivated in India under medicinal licensing. Organized Criminal Groups siphon off this opium to be sold in the illicit market.
Side Topic: Narco-Terrorism
- According to the US Drug Enforcement Administration (DEA), narco-terrorism is “a subset of terrorism,” where groups or individuals participate directly or indirectly in the cultivation, manufacture, transportation or distribution of controlled substances and the money derived from these activities”.
2. Smuggling
- Goods are smuggled in and out of the country by Organized Crime Groups without paying the required taxes and dodging customs.
- The nature of smuggled goods depends on the fiscal policies adopted by the government. E.g., Textile items and electronic items were smuggled in the 1970s. Presently, gold is the primary item that is smuggled into India.
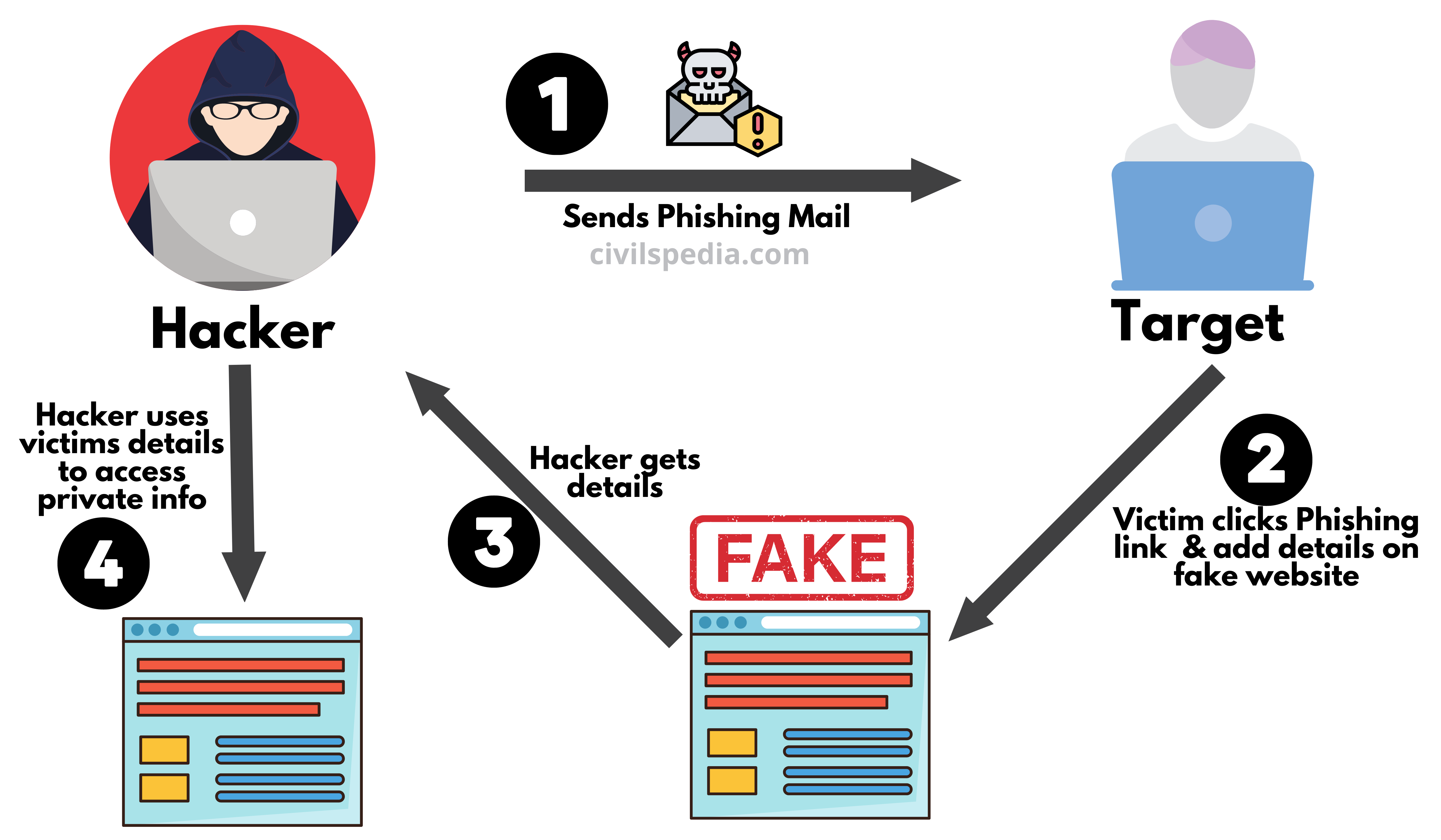
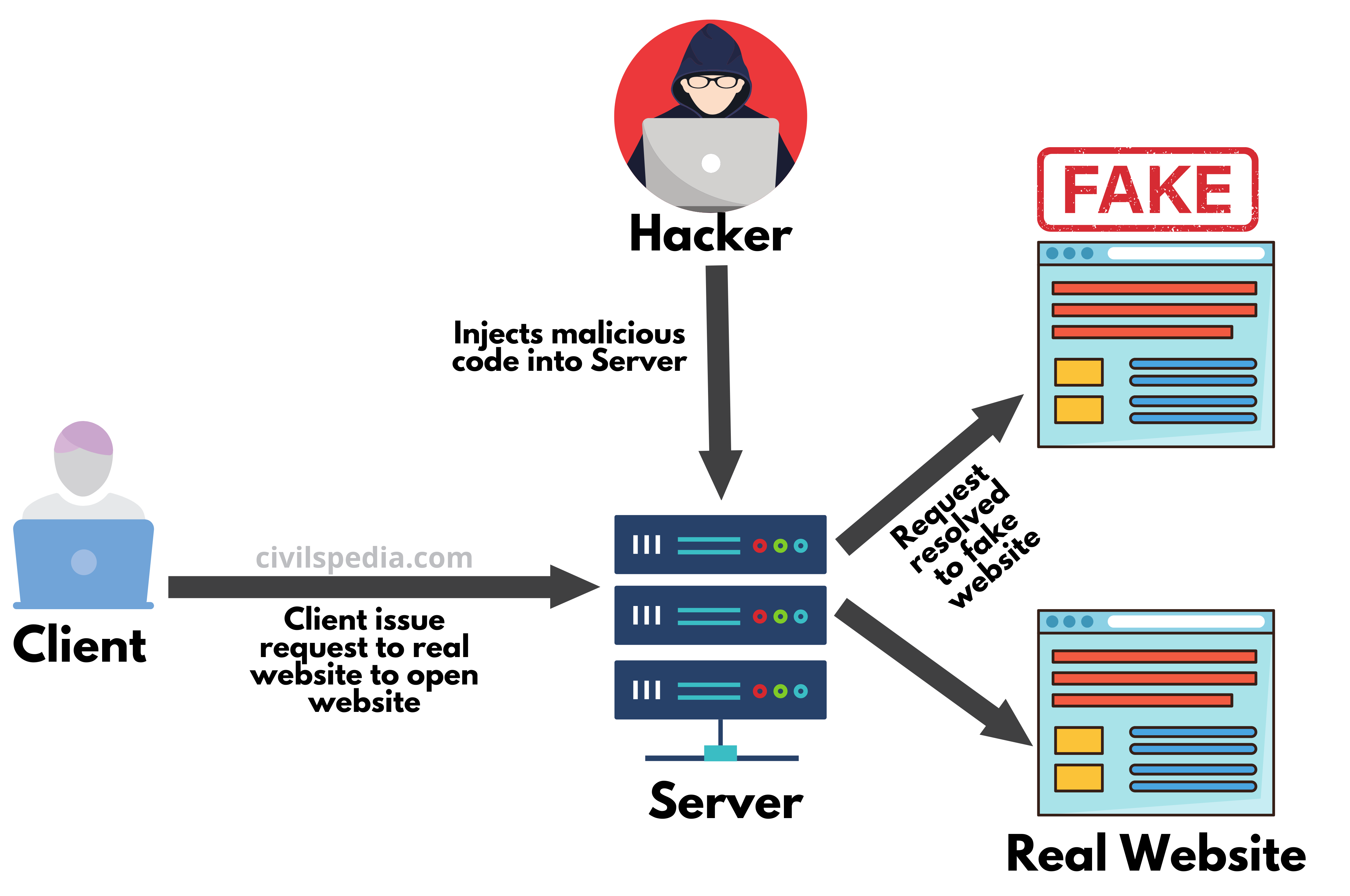
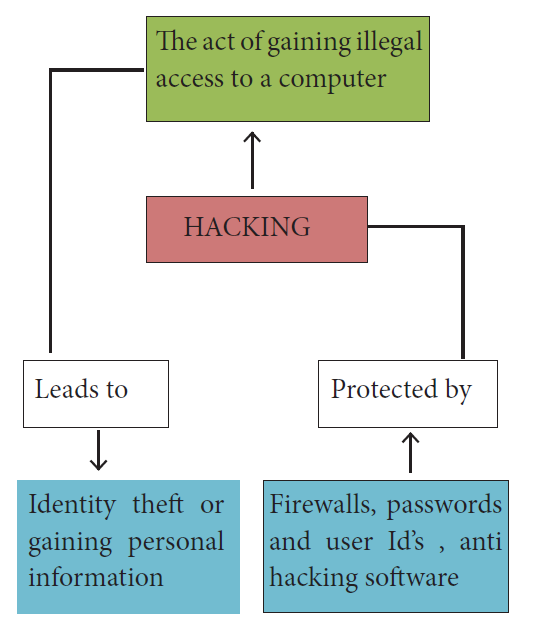
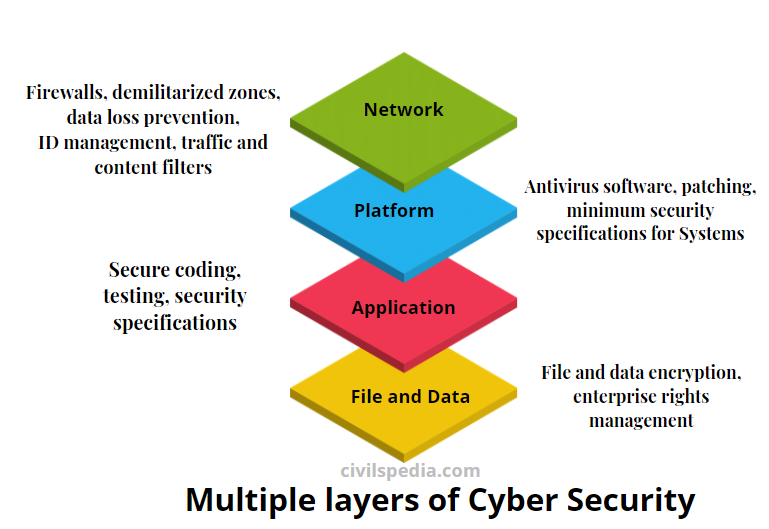
3. Cyber Crimes
- With increased dependence on computers, cyber crimes have emerged as the main activity of Organized Crime Groups. They indulge in hacking, copyright piracy, software piracy, credit card fraud etc.
4. Environmental Crime
- There is a large-scale poaching of animals due to organized crime. 50% of world species are facing the fastest man-made mass extinction because of animal poaching.
- Timber poaching is also a multi-billion dollar avenue and organized crime groups.
5. Trafficking cultural property
- Trafficking of cultural property is a crucial avenue for money laundering. Ancient Artefacts are stolen, and organized crime groups destroy sites to erase the trails of theft.
6. Piracy
- Piracy is widespread across the Horn of Africa, Malacca and Sundarbans.
- Organized crime groups indulge in attacking merchant ships to take the crew hostage and demand money to release the hostages. They earn millions of dollars through this route.
7. Prostitution
- Trading in sex and girl-running is a very profitable business. Underworld is closely connected to brothels and call girl rackets. According to the WHO, Bombay & Kolkata has 1 million, and Pune & Delhi have 40,000 prostitutes.
- It has to be noted that prostitution per se is not an offence in India. However, running brothels, inducing girls for the sake of prostitution, detaining girls in brothels, or running brothels in the vicinity of public places is a criminal offence.
8. Contract Killing
- Organized Crime Groups like D-Company and Yamaguchi Gumi are also involved in contract killing. They are ready to kill anybody in return for specific fees. It is also the preferred mode of killing, as the conviction rate in contract killing is negligible.
- Under the contract, the part amount is paid in advance, called ‘supari’. The rest of the payment is made after the commission of the crime.
9. Money Laundering
- Money laundering means the conversion of illegal and ill-gotten money into legal money. Organized Crime Groups provide services via placement, layering and integration of black money in return for fees.
10. Kidnapping
- It is a highly organized crime. Crime groups kidnap children or adults and demand huge sums in return for releasing them.
- This activity is mainly carried out in urban areas.
11. Organ trafficking
- An organ transplant can save a life, but there is a heavy demand-supply mismatch. Due to the desperate situation of the recipient, they are ready to pay a hefty amount. Organized Crime groups exploit this situation by indulging in organ trafficking.
- Unlike other crimes, professionals like doctors, nurses etc., are also involved in this.
12. Light Arms Proliferation
- Light arms proliferation is a global phenomenon. It has taken a heavy toll on entire regions’ lives and socio-economic development.
- Organized Crime Groups are the main suppliers of illegal light arms like pistols, guns etc.
13. Intellectual Property Crime
- Intellectual Property Crime (IPC) includes the manufacturing, storage and sale of counterfeit or pirated goods where the consent of the rights holder has not been obtained.
- Some scholars argue that it constitutes the largest black-market economy, surpassing the global narcotics trade.
Organized Crime and Terrorism
The intersection between terrorism and organized crime can be divided into three categories
1. Co-existence
- It refers to the situation when both (Organized Crime Gangs & Terrorist Organisations) operate in the same theatre but remain separate entities.
2. Cooperation
- Generally, Organized Crime Groups and Terrorist organizations don’t cooperate as their motives differ. While Terrorists want a change in the political status quo, Organized Crime Groups want a change in the status quo only when it threatens them.
- But when the benefit outweighs the risk, they cooperate, including specific operational supports which can be acquired cost-effectively from each other. E.g.:
- In Columbia, Medellin Drug Cartel hired ELN to implant car bombs because they didn’t have the expertise in bombs.
- Islamic Movement of Uzbekistan allied with the Afghan drug mafia so that movement of drugs could occur safely to the Soviet Union.
- Terrorist Organizations frequently use Organized Crime Groups’ help to create fake passports, smuggling terrorists into countries. Terrorist groups / Insurgents active in the North-Eastern States take the services of crime syndicates active in Cox Bazaar for such activities.
3. Confluence
When a single entity does both activities
| Organized Crime | When Organized Crime Group uses terror tactics to safeguard their business interest. E.g., D-Company’s terrorist activities. |
| Terrorist Group | When Terrorist Group uses organized crime to gather funds, E.g., Al Qaeda uses drug trafficking, and ISIS uses women trafficking to fund their activities. |

It is also known as ‘Black Hole Syndrome‘, where terrorist groups and transnational organized crime groups converge entirely into each other. The black hole syndrome is thus described as the natural progression of these two criminal groups gaining economic and political control over the territory (Tamara Makarenko, 2005, p.129)
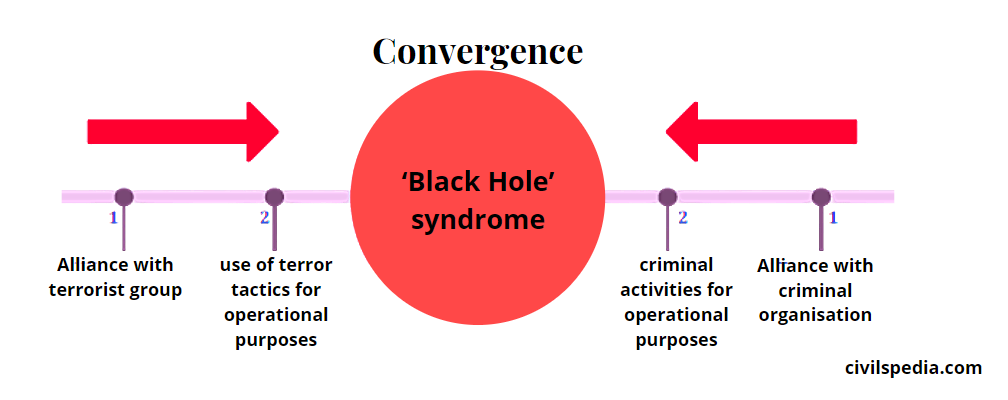
Indian examples of Black Hole Syndrome
- In the Northeast, extortion, drug trafficking and gun running are the fundamental basis for funding terrorism.
- D Company of Mumbai (as discussed above).
Similarities between Terrorism and Organized Crime

- There is a similarity in personality traits of members belonging to terrorist organizations and Organized Crime Groups. Members of both organizations are
- From the marginal social groups exposed to and burdened by social or political frustrations
- They are the persons attracted by excitement and thrill.
- They have risk-taking ability.
- Terrorist Organizations and Organized Crime Groups have similarities in their modus operandi, which involves
- Secrecy and confidentiality.
- Use of violence to accomplish certain goals or interests.
- Detailed planning and preparation
- Respect for strict discipline.
- Intimidating the surroundings.
- Activities carried out by both, i.e. Terrorists and Organized Crime Groups are punishable by law.
Differences between Terrorism and Organized Crime
| Terrorist Organisations | Organized Crime Groups |
| They want to overthrow the existing government by changing the present order. | They don’t want to overthrow the state => Only want to form a parallel government. |
| They use violent means. | These groups generally remain non-violent. Violence is used as a last resort. |
| Terrorists are driven by political objectives. | Organized Crime Groups are driven by economic objectives, devoid of any political dimension. |
| Terrorist organizations claim responsibility for terrorist attacks. | Organized Crime Groups never claim responsibility for their criminal acts. |
| They try to seek media attention. | They don’t seek media attention and remain low profile. |
| They attack government and law enforcement agencies. | They generally don’t indulge in such activities. |
| They want to influence public opinion. | They aren’t concerned with public opinion. |
UN Convention Against Transnational Organized Crime
- It was adopted in 2000 and came to force in 2003.
- The Convention is supplemented by three supplementary protocols i.e.
- Protocol to Prevent, Suppress and Punish Trafficking in Persons, especially Women and Children
- Protocol Against the Smuggling of Migrants by Land, Sea and Air
- Protocol against the Illicit Manufacturing of and Trafficking in Firearms and Ammunition
- As a signatory, the country is committed for
- Creation of domestic criminal offences for participation in an organized criminal group.
- Adoption of frameworks for extradition, mutual legal assistance and law-enforcement cooperation.
- Promotion of training and technical assistance for building or upgrading the necessary capacity of national authorities.
Legal position in India on organized crime
- There is no national law explicitly dealing with Organized Crime in India. Various provisions of IPC deal with it. But the Government of India is planning to make the Organized Crime Control Act.
- Various states have enacted special legislation to tackle Organized Crime, like Maharashtra (first to pass in 1999), Delhi, UP, Gujarat, Karnataka & Haryana (2019).
1 . Provisions of IPC
Criminal Conspiracy
- It is defined by Section 120A of IPC.
- Criminal Conspiracy is – when two or more persons agree to do or cause to be done an illegal act or an act which is not illegal by illegal means.
Dacoity
- Section 391 of IPC deals with it.
- If 5 or more persons commit a robbery, it is termed as dacoity.
- It is a punishable offence with imprisonment for life or rigorous imprisonment of up to 10 years.
2. Provisions to tackle Human Trafficking (by Organized Crime Groups)
- Anti-Trafficking Nodal Cell has been set up by the Ministry of Home Affairs to act as a focal point for tackling Human Trafficking in the country.
- The government of India has also signed agreements with Bangladesh, Nepal, Bahrain etc., to curb Human Trafficking.
3. Provisions to tackle Drug Trafficking (by Organized Crime Groups)
- Acts: India has enacted the Narcotics Drugs and Psychotropic Substances Act, 1985 (NDPS Act) and the Prevention of Illicit Trafficking of Narcotics Drug and Psychotropic Substances Act, 1988.
- International Conventions: India is a signatory to all three UN Conventions, namely
- Convention on Narcotics Drugs, 1962
- UN Convention on Psychotropic Substances, 1971
- UN Convention against Illicit Trafficking of Narcotics Drug and Psychotropic Substances Act, 1988
4. State Acts
- Various states have passed State laws to control organized crime, notorious gangsters and crime syndicates in the state. Most notable among them is the Maharashtra Control of Organized Crime Act (MCOCA), 1999.
5. Suggestions of the Supreme Court
- Supreme Court has recently directed the Centre to set up Organized Crime Investigating Agency (OCIA). It can be a positive step in combating organized crime.
Problems in controlling Organized Crime in India
- Inadequate Legal Structure: India needs a special law to control/suppress organized crime. The existing law is insufficient as it targets individuals and not criminal groups or criminal enterprises.
- Difficulties in Obtaining Proof: Organized Criminal groups are structured hierarchically, and the higher echelons of leadership are insulated as there is hardly any documentary evidence against them.
- Dual Criminality: Certain crimes, particularly drug trafficking, are planned in one part of the world and executed in another. Different nations have different legal structures, and the extradition of criminals from one country to other is very difficult.
- Criminal, Political & Bureaucratic Nexus: Due to this, the investigating and prosecuting agencies find it difficult to deal effectively with them.
- Lack of Resources & Training: Police come under the State’s subject. Most States face a resource crunch, and there are hardly any training facilities for investigating organized crime.
- The police force in India is not trained to deal with organized crime. Their training involves dealing with conventional crime, and organized crime is neglected.
- The technological sophistication of organized crimes due to new technologies like cryptocurrencies has opened up many possibilities for criminals to carry out traditional crimes without leaving a trail.
- Weakness of the financial system due to the prevalence of the cash economy, parallel transactions through hawala, money laundering etc., makes it harder for law enforcement agencies to control them.