Table of Contents
Security challenges and their management in border areas
This article deals with ‘Security challenges and their management in border areas.’ This is part of our series on ‘Internal Security’ which is an important pillar of the GS-2 syllabus. For more articles, you can click here.
Introduction
- Borders are the visible symbols of a country’s sovereignty, unity and integrity.
- There are three distinct sets of borders at the international level i.e.
- Land borders
- Maritime boundaries
- Airspace
- Border security in the present world order is a complex proposition. The transgressor is always on the lookout for soft gaps on land, along the coast and, if need be, from the air. Therefore, adopting a holistic approach to border security is necessary.
- In this chapter, we will read about Border Management, a broader term than Border Security. While Border Security Approach deals only with defending the borders, Border management is a broader term which involves defending the borders and protecting the country’s interests in aligning borders.
- India has a huge land border of 15,106 km and a coastline of 7,516.6 km, including island territories.
- India has specialized forces to guard the borders apart from the Indian Army. Assam Rifle, Border Security Force, Indo-Tibetan Border Police and Shashatra Seema Bal are India’s Border Guarding Forces.
Borders and Issues
Some general issues faced in the management of Indian borders include
- No proper demarcation of maritime and land borders in many places, which leads to conflicts
- Artificial boundaries which are not based on natural borders are difficult to guard. E.g., In Punjab, an artificial line was created dividing united Punjab, and there is no river or mountain dividing the two countries.
- Multiplicity of forces on the same borders leads to problems of coordination, command and control.
- India has a separate force to manage different borders, which leads to a silos approach to border management. In other countries (as shown below), there is a single specialized and dedicated force for managing all the borders.

- Cross-border terrorism targeted to destabilize India.
- Border Guarding Forces like Border Security Force lack infrastructure, including the latest guns, night vision glasses etc.
- Hostile elements have access to the latest technology and advanced weapons.
- Illegal migration in the north-eastern region causing demographic changes and social backlashes between the migrants and indigenous people
- Due to the porous nature of the border, smuggling of arms, narcotics and counterfeit currency happens rampantly.
Task Force on border management under the Chairmanship of Madhav Godbole has also concluded that the country’s borders could not be effectively managed because of inherent problems such as their disputed status, artificiality and porosity.
General Recommendations regarding better Border Management
- Use of advanced technology for surveillance, particularly satellite and aerial imagery.
- The Border Security Force (BSF) should be responsible for the security of all settled borders, while the responsibility for unsettled and disputed borders should be that of the Indian Army.
- For effective accountability, the principle of ‘single point control’ or ‘one-force-one-border’ must be followed.
- Infrastructure along the border should be developed at an accelerated pace, especially to wean the border population from illegal activities.
- Upgradation of the intelligence network along the border should be the utmost priority.
- Raising the issues of infiltration across the border during various meetings with the counterparts.
- Establishment of more Integrated Check Posts (ICP) at the land borders, which house all regulatory activities such as immigration, security and customs under one roof. It has to be noted that a Statutory Authority called ‘Land Ports Authority of India’ (LPAI) has been set up to oversee and regulate the construction, management and maintenance of the ICPs.
Bangladesh
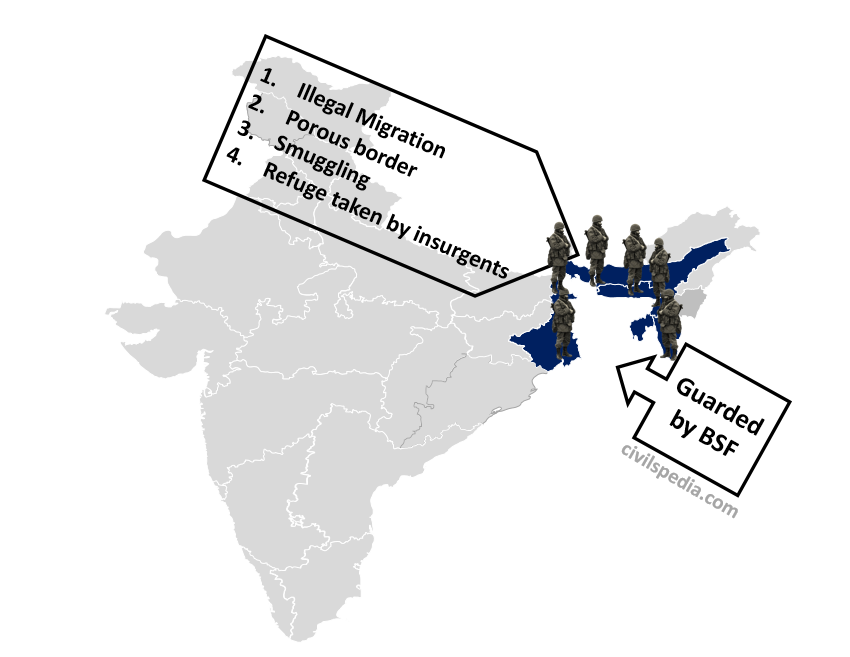
General Information
| Bordering states | West Bengal, Assam, Meghalaya, Tripura and Mizoram |
| Guarding force | Border Security Force (BSF) |
Problems
- Illegal migration to West Bengal and Assam has changed the demographic profile of the region.
- Inadequate border fencing due to issues such as the riverine nature of the border, pending land acquisition cases and protests by the border population. Hence, there is a high degree of porosity.
- Smuggling of goods like jamdani sarees, rice salt and livestock (especially cattle) etc. According to a CBI investigation (2021), BSF officials take a bribe of ₹2000 per cattle to allow the smuggling of Indian cattle to Bangladesh.
- North-East Insurgents take refuge in Bangladesh due to the porous border.
- India and Bangladesh share 54 transboundary rivers. As a result, there are various water disputes, such as sharing of the waters of the Teesta river and the construction of a dam on the Barak river by India.
- Radical groups like Harkat-al-Jihad-al-Islami (HUJI) and Jamaat-e-Islami fuel Anti-India sentiments in Bangladesh. Their propaganda could spill across the border.
- The border area is densely populated, and people on both sides live in close proximity to the border.
Recent Initiatives
- The government has announced the establishment of a Border Protection Grid (BPG) consisting of BSF, State Police, Army etc.
- Installation of border surveillance devices such as closed-circuit cameras, searchlights, thermal imaging devices and drones to keep a tight vigil on the border.
- Parliament has passed the 100th Constitutional Amendment to solve the issue of Adverse Possessions and landlocked enclaves amidst other’s territory.
- Border Haats, i.e. traditional markets of local produce that can be accessed by people from across the border, have been established at the Indo-Bangladesh border. Trade can be carried here using Indian Rupee or Bangladeshi Taka.
- Project BOLD-QIT (Border Electronically Dominated QRT Interception Technique) has been started to install different kinds of sensors in the unfenced riverine area of the Brahmaputra and its tributaries.
- Road construction: 3,585.53 km of border patrol roads have been constructed on Indo-Bangladesh Border.
- Integrated Check Posts (ICPs) have been established at places like Sutarkandi in Assam and Ghojadanga in West Bengal along the Bangladesh border.
- Border forces of the two countries also undertake joint exercises such as ‘Sundarbans Moitry’ (Sundarbans Alliance) for better coordination in border management.
China
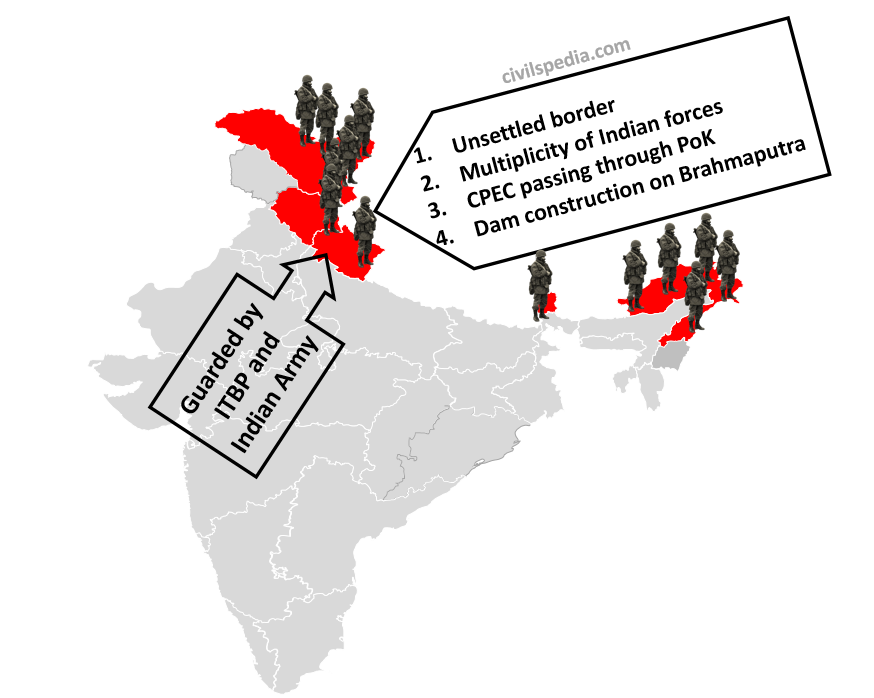
General Information
| Bordering states | UT of Ladakh, Himachal Pradesh, Uttarakhand, Sikkim and Arunachal Pradesh |
| Length | 3,488 km |
| Guarding Force | Indo-Tibetan Border Police Force (ITBP) together with the Indian Army. |
Issues
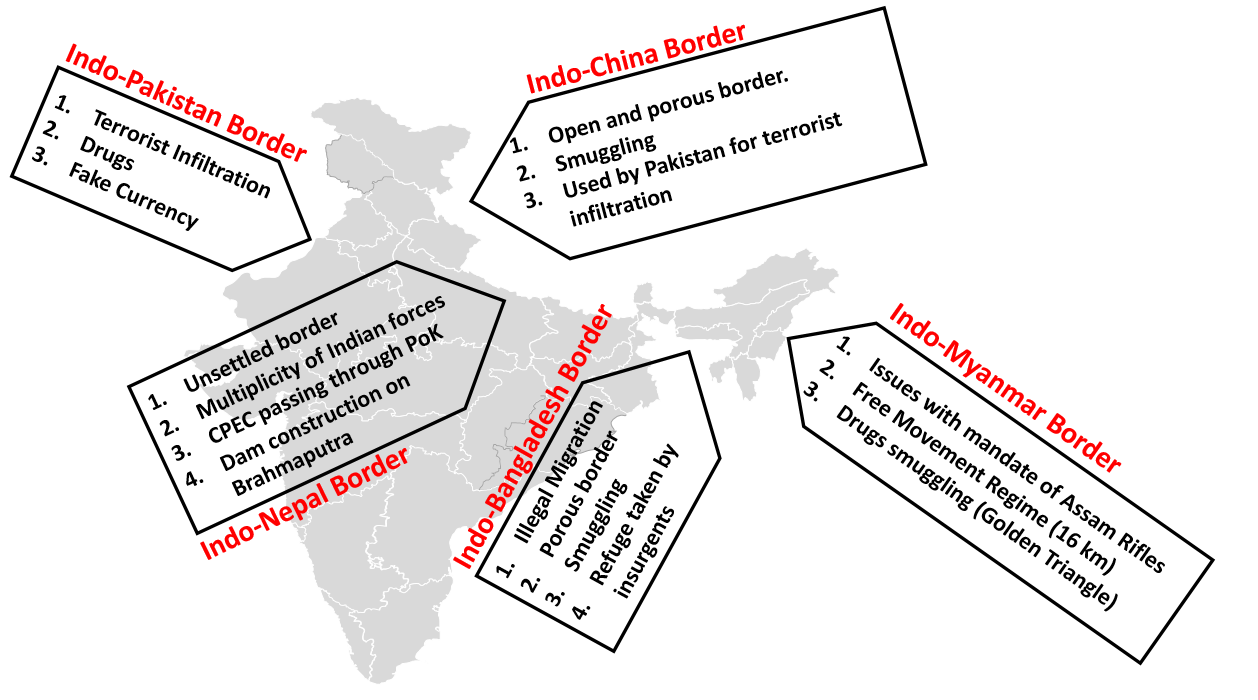
- Border dispute at Aksai Chin in Ladakh and Arunachal Pradesh with sporadic aggression by the Chinese Army (PLA).
- Large-scale smuggling of Chinese electronics and consumer goods occurs on the Sino-India border.
- Inadequate infrastructure due to high altitude and thick habitation. However, China has undertaken a large-scale upgradation to air, road and rail infrastructure.
- Multiple forces along the Indian border (ITBP, Assam Rifles and Special Frontier Force) as opposed to a single commander on the Chinese side.
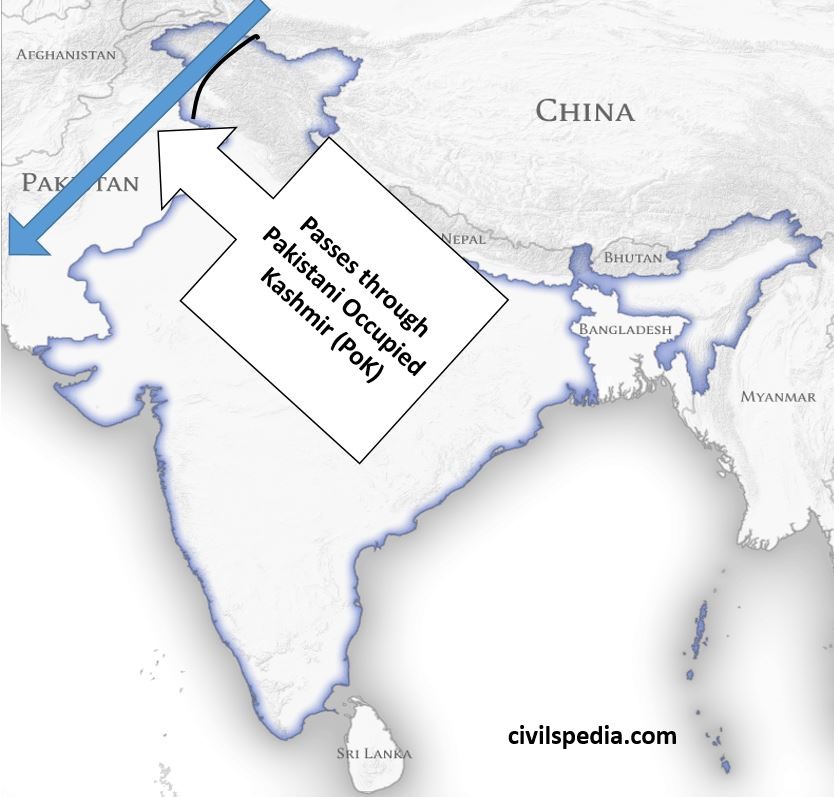
- China’s CPEC passes through parts of Jammu & Kashmir illegally occupied by Pakistan. China can use CPEC to mobilize troops in case of conflict.
- China is building a series of dams on the Brahmaputra river, which is the lifeline of North-Eastern states as well as Bangladesh. Given the Chinese track record on the Mekong river, where China virtually stopped the river flow in South-East Asian countries, this development is worrisome.
Recent Initiatives
- Creating infrastructure: India is constructing critical infrastructure, such as the Dhola-Sadiya bridge, to cut down time for troop movement.
- India is collaborating with Japan to develop infrastructure projects in the North-East to contain China.
- Army infrastructure projects within 100 km of LAC have been exempted from forest clearance.
- The Ministry of Defence has delegated administrative and financial powers to the Border Roads Organisation (BRO) to expedite the border road construction.
Pakistan
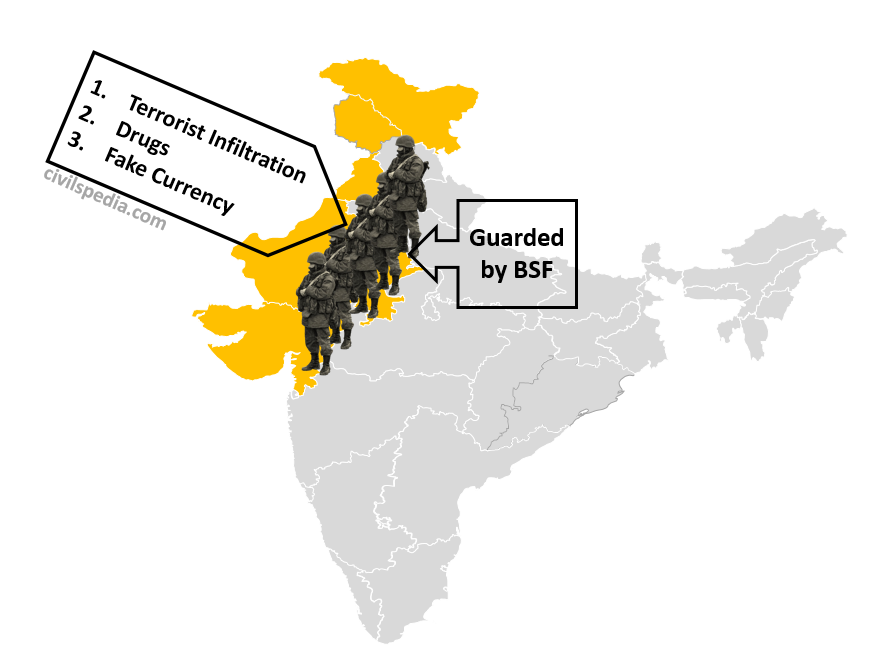
General Information
| Bordering states | J&K, Punjab ,Rajasthan and Gujarat (Boundary between India and Pakistan is known as Radcliffe Line) |
| Length | 3323 km |
| Guarding Force | Border Security Force (BSF) |
Problems
- Border dispute at Sir Creek and Kashmir.
- Cross-border terrorism, especially in Kashmir, to destabilize India.
- Ceasefire violations and frequent shelling.
- Diverse terrain, which includes desert, sea, snow-capped mountains, and plains, makes border guarding difficult.
- Illegal activities like smuggling, drugs and arms trafficking due to porous border.
Recent Initiatives
- After the Pathankot terrorist attack, the Ministry of Home Affairs sanctioned and installed Comprehensive Integrated Border Management System (CIBMS) to safeguard and control the incidents of border infiltration.
- Fencing: By 2011, almost all of the border– along Jammu & Kashmir, Punjab, Rajasthan and Gujarat – has been double-row fenced.
- Outposts: About 700 border outposts and one Integrated Check post at Attari (Amritsar) have been functional.
Nepal
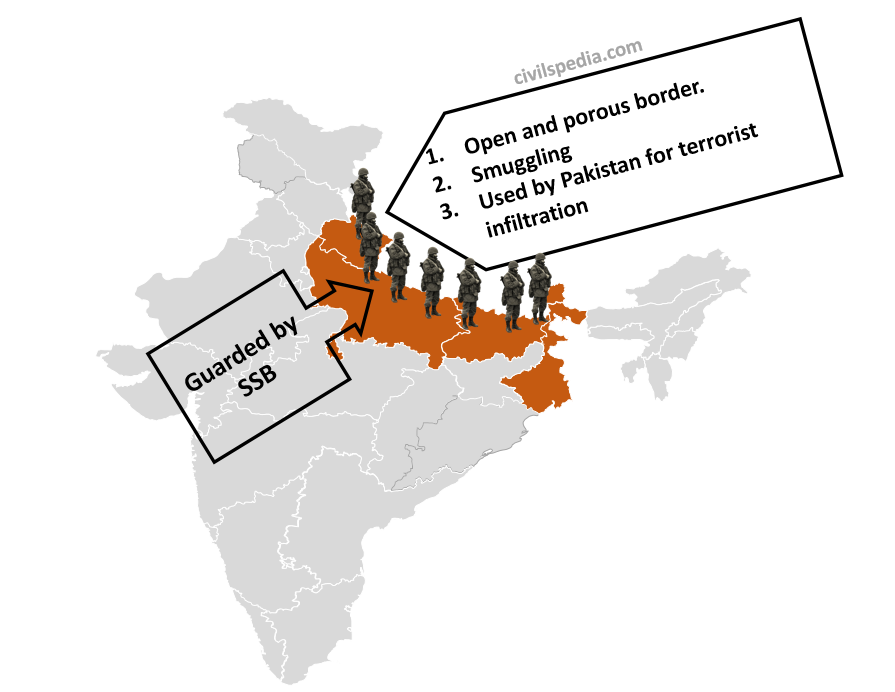
General Information
| Bordering States | Uttarakhand, Uttar Pradesh, Bihar, West Bengal and Sikkim |
| Length | 1751 Km |
| Guarding Force | Sashastra Seema Bal (SSB) |
It must be noted that Nepal’s border is an open border and was virtually unattended until very recently.
Problems
- The highly porous nature of the Indo-Nepal border leads to cross-border crimes. Due to open borders, insurgents and hard-core criminals in both countries crossover to another country.
- Smuggling of essential items, fake Indian currency, gun-running, and drugs and human trafficking happens via the Indo-Nepal border.
- Pakistan uses open borders to carry out anti-India activities, including pushing terrorists and fake Indian currency.
- Fear of the spread of Maoist insurgency due to links of Nepali Maoists in India.
New Initiatives
- Establishment of a new intelligence section in Sashastra Seema Bal (SSB).
- A total of 25 battalions of Sashastra Seema Bal have been deployed on Indo-Nepal Border.
- Border District Coordination Committee at the district level of two countries has been established.
- The government of India has approved the construction of 1377 km of road along the Nepal border.
- India is giving development aid to Nepal.
Myanmar
General Information
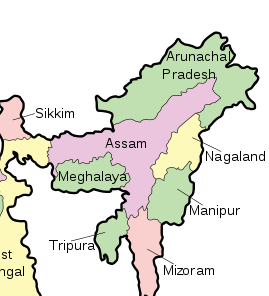
| Bordering States | Arunachal Pradesh, Manipur, Mizoram and Nagaland |
| Length | 1,643 km |
| Guarding Force | Assam Rifles |
Problems
- Assam Rifle is mandated to preserve peace in the North East and guard Indo-Myanmar Border. Consequently, they are unable to do both works professionally. The government should correct this anomaly by either giving it the single mandate of guarding the Indo-Myanmar border or deploying some border guarding force like BSF to guard the Indo-Myanmar border. In 2017, Parliamentary Committee on Home Affairs, in its report, suggested the transfer of Indo-Myanmar Border Management to Border Guard Forces (BGF) instead of Assam riffles for better management.
- The highly porous border with Free Movement Regime up to 16 km (explained below)
- About 170 km of the border is not properly demarcated.
- A porous border due to the absence of a physical barrier is exploited by Indian insurgent groups, which use Myanmar as a safe haven (Naga insurgents, especially NSCN-K, use this).
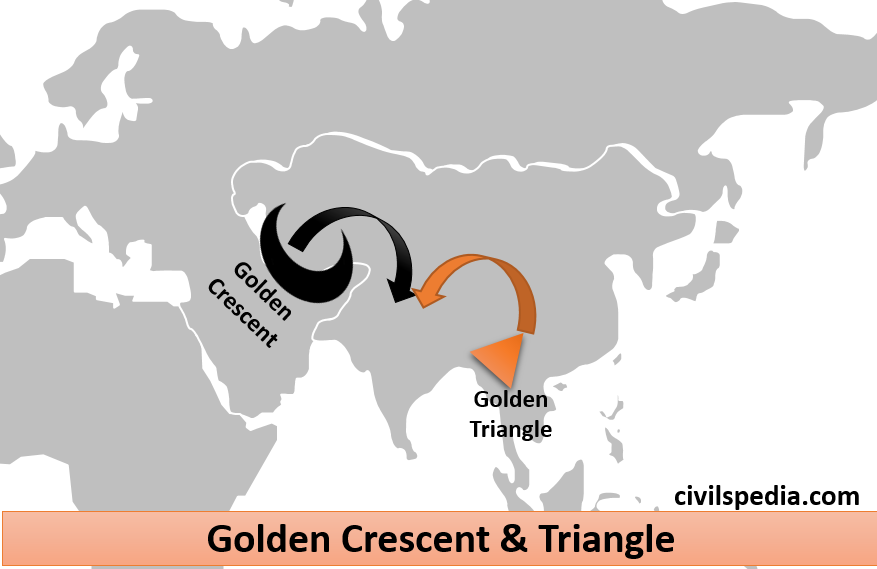
- Drug trafficking due to proximity to the golden triangle. Majority of heroin enters India through the border town of Moreh in Manipur.
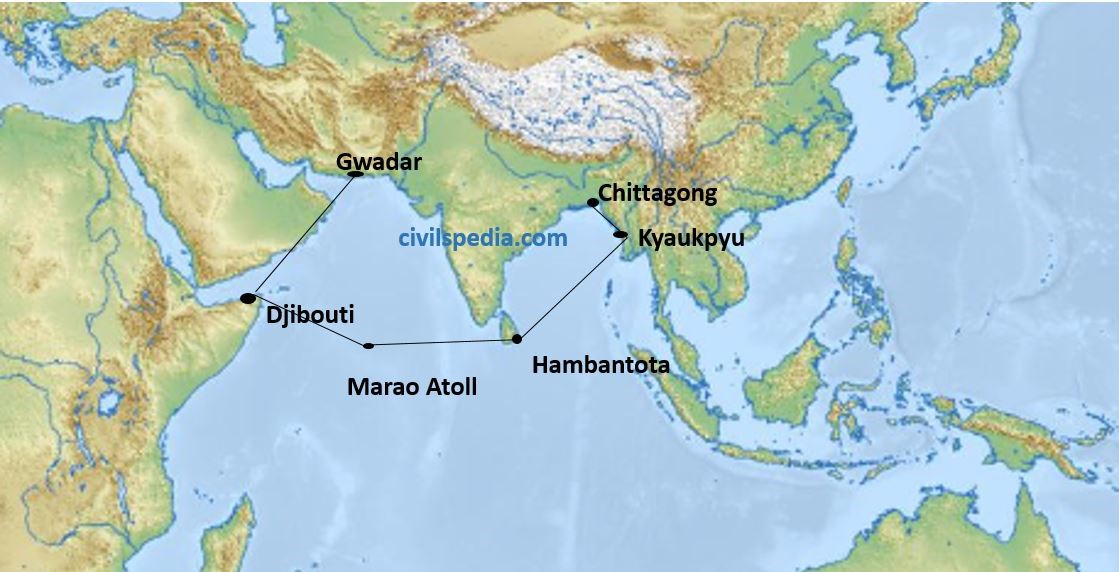
- China’s interest in Myanmar is also a threat to India as it is building Kyaukpyu port in Myanmar as part of the ‘String of Pearls’ strategy to encircle India.
- During the 2021 coup d’etat by Myanmar Military, a large number of people crossed over to India in fear of political persecution. It created a large rift between the Union Government, which wanted to stop the refugees from entering India and the Mizos, who share ethnic ties with Chins and who wanted to give them safe havens.
Free Movement Regime (FMR) Issue
Tribal Naga and Mizo communities claim that the boundary between India and Myanmar is inconsistent with the traditional limits of the region they inhabited. They continue to have trans-border linkages with their kiths and kin. FMR is thus an arrangement to alleviate the insecurity of tribals living along the India and Myanmar border. It permits tribes residing along the border to travel 16 km across the boundary without visa restrictions.
Issues with FMR
While the FMR has helped the tribes maintain their age-old ties with their kin on the other side of the border, it has become a cause of concern for the security establishment.
- Militants and criminals misuse FMR for infiltration, smuggling weapons, narcotics, trafficking of women and children etc.
- Militants groups such as the NSCN-K, NSCN-IM, ULFA etc., exploit this to get safe havens in Myanmar.
- The exodus of Rohingyas: Rohingyas also entered India using this route.
Note: In 2015, India carried out surgical strikes against NSCN-K in Myanmar by crossing the border in response to the insurgents’ killing of a troop contingent. But this raises the issue of Sovereignty versus National Security and the question of whether the national security of one country can be given precedence over the sovereignty of the other country.
Bhutan
General Information
| Guarding Forces | Sashastra Seema Bal (SSB) |
| Bordering States | Assam, Arunachal Pradesh, Sikkim and West Bengal |
Problems
- The border between Bhutan and China is not demarcated at the tri-junction of India, Bhutan and China. There is a border dispute over Doklam, which is dangerously close to Chicken’s neck and can jeopardize the security of the entire Northeast.
- Insurgent groups such as Bodos, ULFA etc., sneak into Bhutan for sanctuary.
- Smuggling of goods such as Bhutanese cannabis, liquor and forest products from Bhutan to India and livestock, grocery items and fruits from India to Bhutan
- Free movement of people and vehicles
- Migration trigger fear of change in demography in Bhutan. Migrants are also accused of deforestation, poaching, and wildlife smuggling.
New Initiatives
- Cooperation with the Bhutanese army to prevent sanctuary to insurgents on their soil. Operation All Clear was undertaken by Bhutan and Indian forces in this regard.
- The government of India has approved the construction of a 313 km road in Assam along the Indo-Bhutan border.
- The union environment ministry has given “general approval” for the diversion of forest land for major border infrastructure projects along the eastern border with Bhutan, Myanmar and Nepal.
- India has established new border posts in Sikkim along the Bhutan frontier near Doklam.
- India has established a new intelligence section in SSB.
Sri-Lanka
General Information
- Sri Lanka shares a maritime border with India.
- Tamil Nadu is situated across the Palk Strait and is the most crucial determinant in Indo-Sri Lankan relations.
Problems
- Katchatheevu Island Issue: India ceded the uninhabited island to its southern neighbour in 1974 under a conditional accord. However, Tamil Nadu and the fisherman community still argue it is their traditional fishing area.
- Trespassing by Indian fishermen in Sri Lankan waters takes place regularly. Here, the issue is not of an unsettled maritime boundary but the refusal of Indian fishermen to recognize the maritime boundary between India and Sri Lanka, especially in Palk Bay.
- Although LTTE and Tamil insurgency in Sri Lanka has been completely eliminated, supporters of the Tamil cause in Sri Lanka are still active in the Indian state of Tamil Nadu.
New Initiatives
- All big trawlers (20 meters and above) are being installed with AIS transponders.
- Distress Alert Transmitters (DATs) are being provided to fishermen to alert the ICG if they are distressed at sea.
Techniques of effective Land Border Management
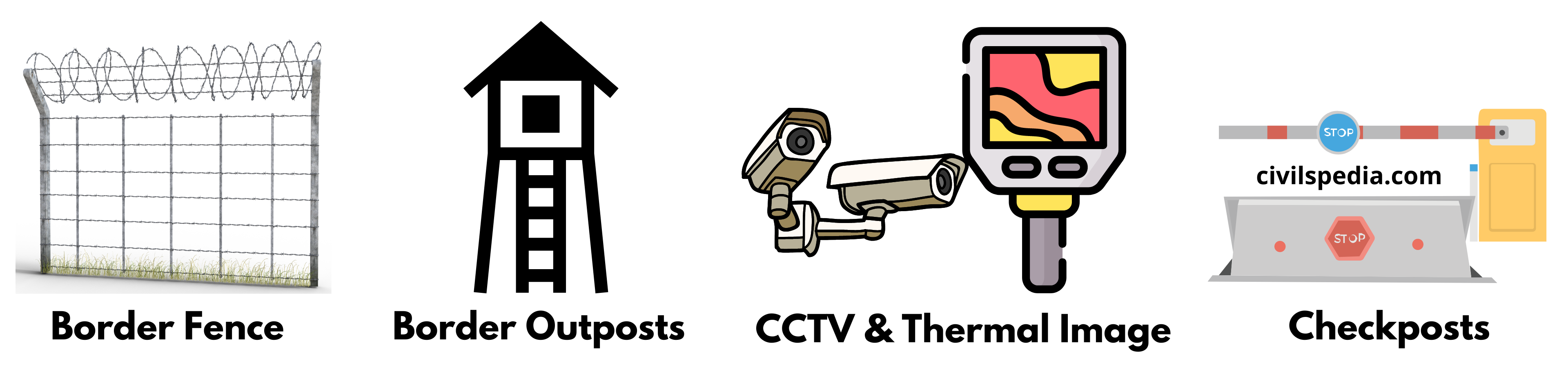
Following are the techniques of effective land border management
- Building fences and erecting floodlights.
- Creating effective Border Out Posts (BOPs).
- Set up border infrastructure like roads for effective mobilization during the time of need.
- Effective patrolling and building of observation post towers.
- Building of nakas and checkposts.
- Equipping the security forces with night vision technologies.
- Installation of CCTV & thermal imaging equipment on the border.
Issues faced by Border Guarding Forces (BGF)
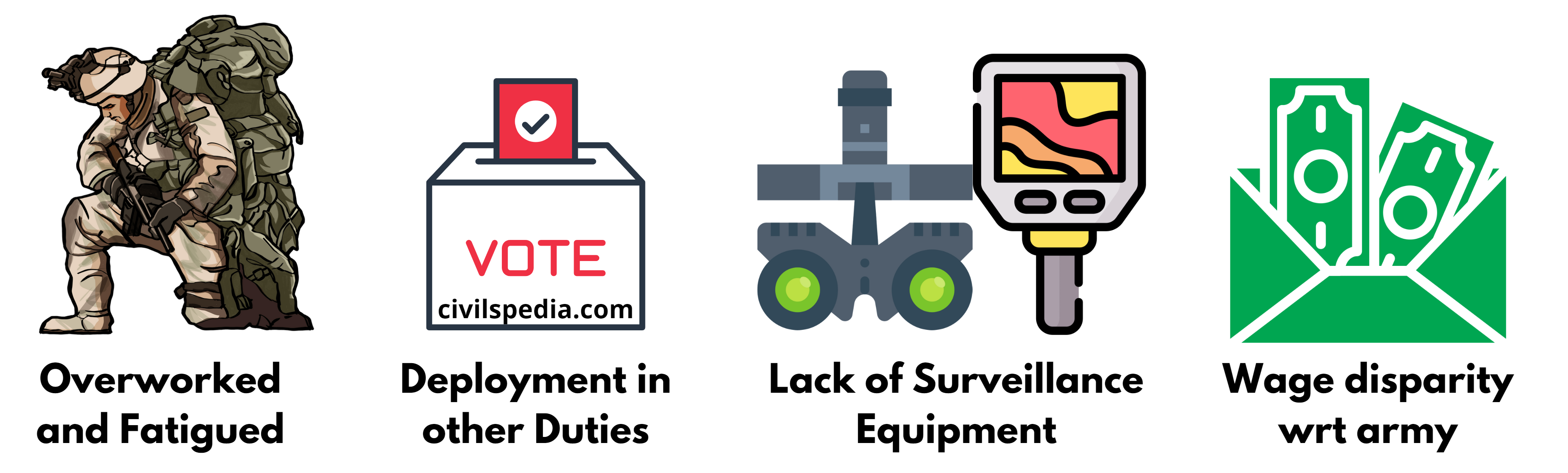
BSF, SSB, ITBP etc., are the Border Guarding Forces. These forces face various issues, as mentioned below.
- Jawans are overworked and hence fatigued during patrolling duty.
- Deployment of BGF Battalions to duties other than guarding the borders, like conducting elections
- Deficiency of surveillance equipment, like hand-held Thermal Imagers, which are essential for surveillance during night
- Inadequate medical facilities, and they are transferred to Frontier Headquarters for even basic treatment.
- Disparity in wages compared to the army.
Government response/Steps taken by the government
1. Comprehensive Integrated Border Management System (CIBMS)
Madhukar Gupta Committee was constituted against the backdrop of the Pathankot attack. In this attack, terrorists attacked the army installation after infiltrating Indo-Pakistan Border. It recommended the installation of CIBMS to avoid such misadventures of Pakistan-based terrorists. Presently, the system is operational at important points.
Details of CIBMS
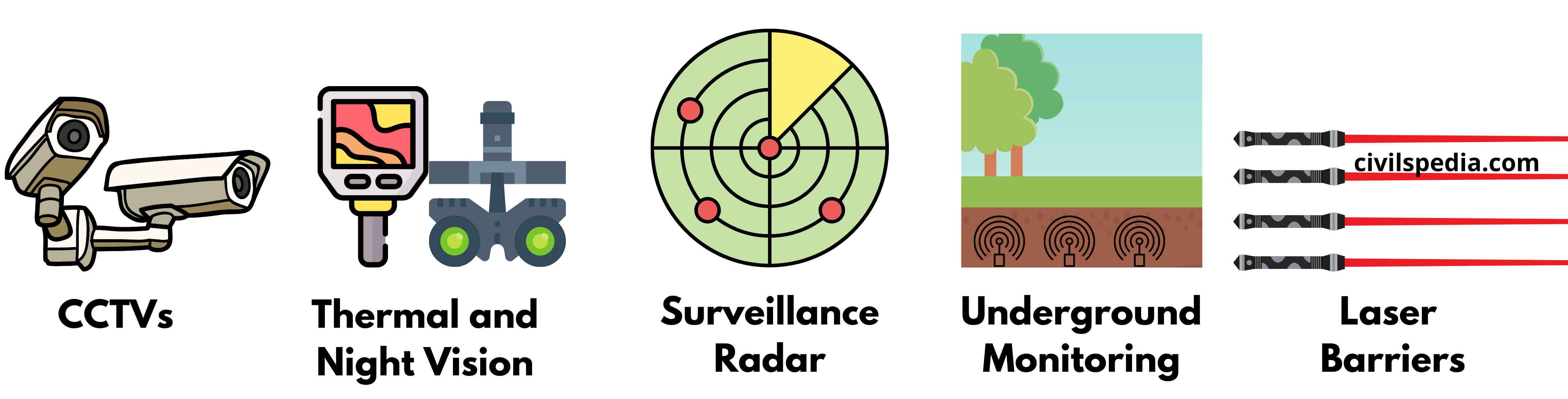
- It is a five-layer elaborate plan to stop infiltration on the western border with Pakistan completely.
- Five layers include
- CCTV cameras.
- Thermal image and night-vision devices
- Battlefield surveillance radar.
- Underground monitoring sensors.
- Laser barriers.
- The integrated setup will ensure that if one device doesn’t work, another will alert the control room in case of a transgression. It will work as a ‘Smart Fence‘.
- Its cost is estimated to be Rs. 1 crore per km.
Side Topic: Use of Technology in Border Management
- Effective border surveillance can be done using CCTV, thermal & radar imagery.
- Drones are used by border guarding forces for aerial surveillance.
- Satellite Monitoring is also used for this. E.g., India is using GSAT-7A & Cartosat for this purpose.
- IRNSS/NAVIC (Indian GPS) provides location services in rugged terrain in the Himalayan borders with Pakistan, China, Nepal and Myanmar.
2. Department of Border Management Division
- Department of Border Management works under Home Ministry.
- It was set up in Jan 2004 on the recommendation of the Godbole Report (formed in the backdrop of the Kargil war to strengthen border management).
- It specifically looks at border management and implementation of the Border Area Development Program (BADP).
3. Development of Integrated Check Posts (ICPs)
- Integrated Check Posts have been set up at places along the border from where the movement of people and goods takes place.
- ICPs house all regulatory agencies like immigration, customs, border security etc.
- They have facilities like warehouses, hotels, parking, banking etc.
4. Border Area Development Programme(BADP)
- It was started in 7th five-year plan.
- It is a 100% centrally funded program. Along with that, all the allocated funds are fully non-lapsable.
- The Department of Border Management under the Home Ministry is the nodal agency.
- It covers 111 border districts in 17 States.
- BADP covers all the villages within 0-10 Km of the International Border.
Objectives
- To create infrastructure
- To provide economic opportunities to the border people
- To instil a sense of security among them.
Main programs
- Construction of roads.
- Ensure water supply, education and sports facilities.
- Organization of early childhood care etc.
5. Border Out Posts (BOPs)
- Border Out Posts (BOPs) are designated entry and exit points on the country’s international border through which cross-border movement of persons and goods occurs.
- BOPs are also meant to provide an appropriate show of force to deter trans-border criminals, infiltrators and hostile elements from indulging in the activities of encroachment and border violations.
- Each BOP is provided with the necessary infrastructure for accommodation, logistic support and combat functions. It also facilitates trade & commerce.
6. Land Port Authority of India
- It is a statutory authority set up to oversee and regulate the construction, management and maintenance of the ICPs.
- LPAI has been envisaged as a lean oversight body aimed at providing better administration and cohesive management of the cross-border movement of people and goods.
- It would be vested with powers along the lines of similar bodies like the Airports Authority of India.
Further Recommendation
1. Clear Chain of Command
- Presently, different agencies are responsible for the management of the same border. E.g., on Punjab Border, BSF, Indian Army and Punjab Police are involved in this. But this results in a lack of accountability. In case of an accident, every agency starts to blame others.
- Hence, there should be one nodal agency and a clear chain of command.
2. Resolving Governance Problems
- The Ministry of Home Affairs should be the nodal ministry for all borders. Presently, the resolution of border disputes is the responsibility of the Ministry of External Affairs (MEA). Low staffing levels and limited leverage of MEA with state governments restrict its ability to resolve border disputes effectively.
3. Restructuring of border forces
- Assam Rifles: Presently, Assam Riffles perform two functions, i.e. guarding Myanmar Border and maintaining security and peace in North East. There should be a separate Border Guarding Force for the Indo-Myanmar border.
- BSF: BSF guards the Indo-Bangladesh and Indo-Pakistan border. It is recommended that the BSF be constituted into two wings, East and West, for better management due to the different nuances of each border.
- The battalions deployed on border guarding duties should have a significant proportion of local youth in its ranks to exploit their knowledge of the terrain, language etc.
4. Involvement of the Stakeholders
Stakeholders in border areas are
- People living in border areas
- State administration
- Border guarding forces
- Central agencies involved in border development.
5. Modernisation
- At present, border guarding work is excessively manpower intensive. There should be a greater infusion of technology into border guarding functions.
- Madhukar Committee Report has also recommended this, and the installation of CIBMS is a step in that direction. Going further, drones and satellite data should also be used for guarding the borders.
6. Upgrading infrastructure
- Areas, especially along the Chinese region, needs proper infrastructure, especially in Ladakh, Arunachal Pradesh and Sikkim.